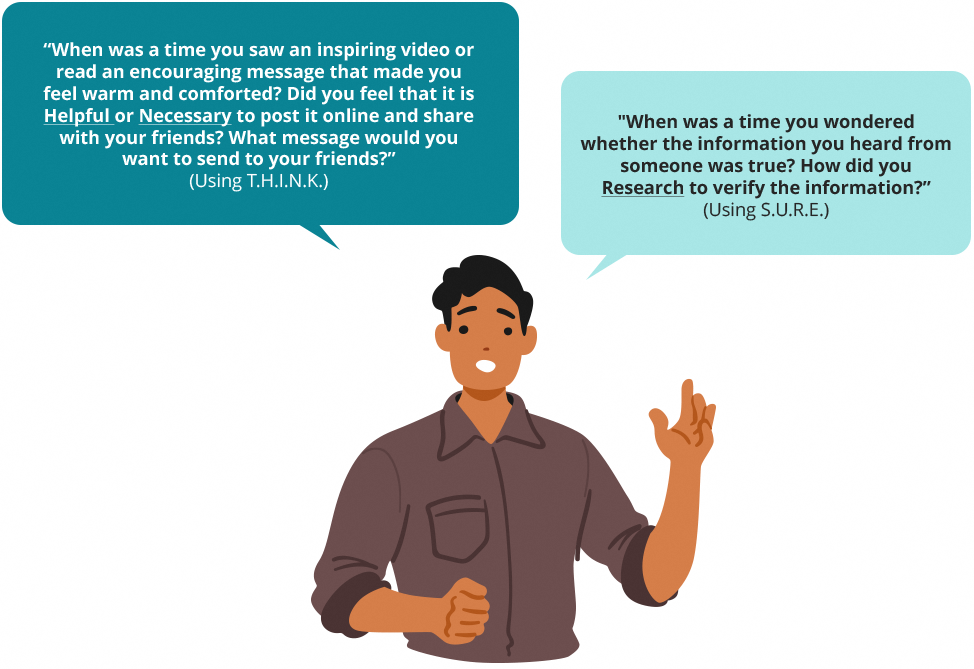
T.H.I.N.K. stands for Truthful, Helpful,
Inspiring, Necessary, and Kind.
Ask your child if what they consider posting online is:

Truthful?

Helpful?

Inspiring?

Necessary?

Kind?
If the answer to any of these questions is ‘No’, they should not post the content online, even if it is intended for their private social media account or a private group chat.
By making it a habit to T.H.I.N.K. before posting anything online, your child can learn to be kind and not hurt others with their online posts.

S.U.R.E. stands for Source, Understand, Research, and Evaluate*.
Before your child shares information they come across online with others,
Source-check to ensure its trustworthiness
Did the information come from credible sources such as people or organisations well-regarded for their expertise in that specific area?

Understand what it is about and if it contains facts and/or opinions
Is the information a fact or someone’s point-of-view? If it is someone’s opinion, is it reliable?

Research other trustworthy sources to cross-check its accuracy
Is the information consistent with other trustworthy sources?

Evaluate it from different angles before deciding if it is trustworthy
Based on what you have learnt from the previous questions, do you think the information is true? Should you share it with your friends and loved ones?

By making it a habit to be S.U.R.E., your child can learn the importance of researching and checking for content accuracy to reduce the spread of misinformation.
To find out more about S.U.R.E., click here.
* S.U.R.E. is part of the National Library Board’s Information Literacy programme.
Additionally, you can encourage your child to use
T.H.I.N.K.
and
S.U.R.E. from young, to reflect on
how they can contribute towards creating a safe and caring online community.
For example, you can ask them: